
Cyber risk (or it risk) refers to any type information technology-related risk. Information technology risks include access risks and data breaches. These risks impact both personal and business data, so they must be managed. This article will inform you about the many risks that IT presents. This article will help you choose the right control measures for your company.
Information technology security
Information technology risk, also known as cyber risk, is any risk associated with information technology. This type of risk is the most prevalent among small businesses and startups, but larger companies must also consider information technology risks to ensure business continuity. Cyber attacks can be mitigated and businesses protected from any negative consequences.
Managing information technology risks requires a systematic and holistic approach. This includes systematic risk assessment and systemic risks management processes. This includes decision-makers willing to reverse prior decisions, a well-defined communications structure, and strong risk-taking.
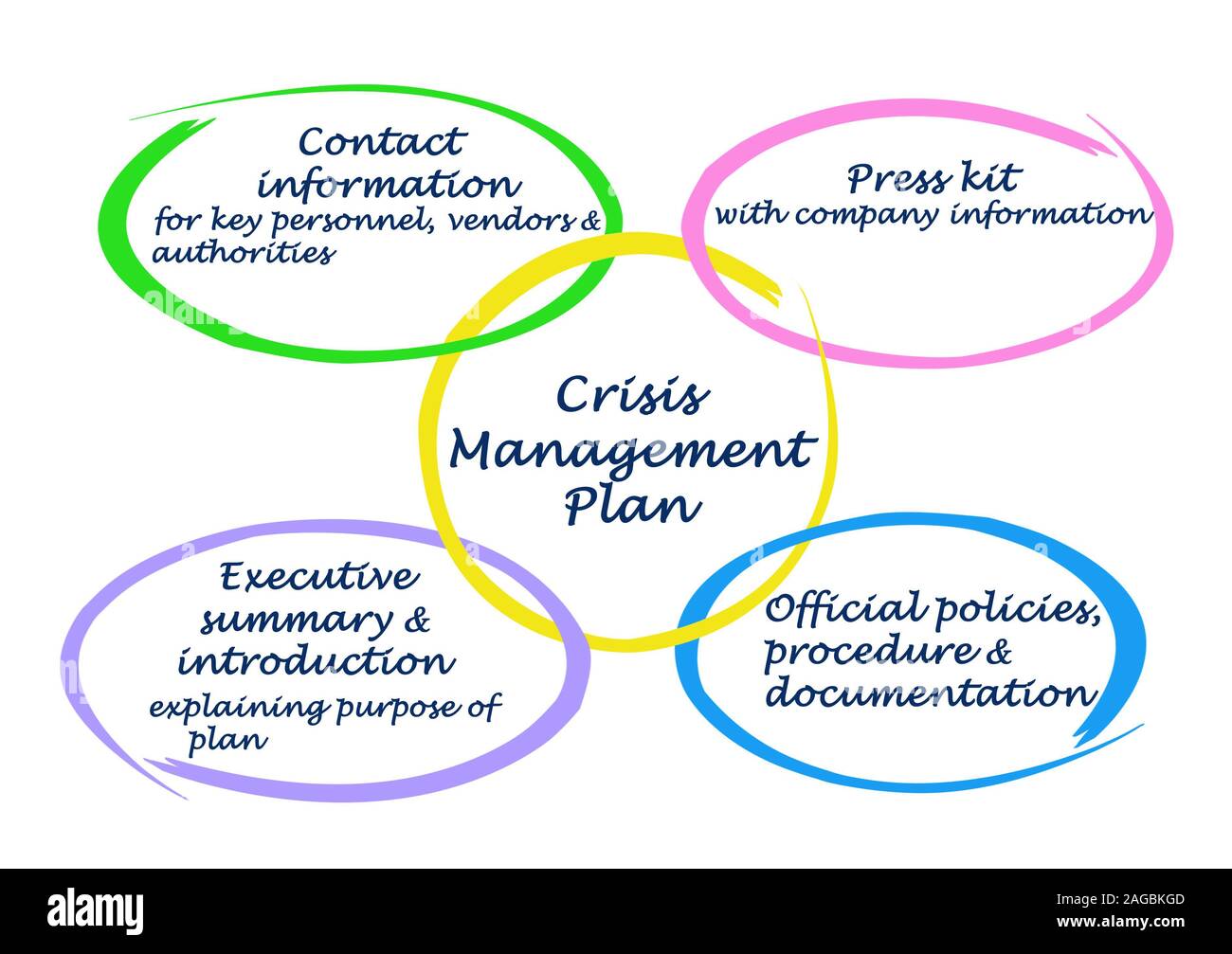
Data breach risk
Unauthorized individuals can access, steal or modify data stored on a computer's system. This is known as a data breach. This can result in financial loss, reputational damage, and lawsuits. It can also lead to security breaches that could compromise government agency systems. High-sensitive information can also be exposed by breaches. A hacker could compromise the government's IT infrastructure and gain access government trade secrets. Private data can also be sold on darknet marketplaces or used by third parties to create fraudulent accounts.
Once an IT risk like a data breach happens, a company should notify its customers and employees and implement a response plan to minimize the negative impact. This plan should be an ongoing document and updated as needed.
Access risk
IT security has to address access risk. It refers the danger of unauthorised access to vital data. Access can occur from both logical or physical access. Physical access involves accessing sensitive information such as databases and processing environments. The network is used to connect users to these systems. Through this network, an employee could gain unauthorized access to confidential and proprietary data.
It can be complex to manage access permissions. Because of the many permission models used by different applications and systems it can be challenging to assign correct permissions for each user. To reduce the risk, organizations can set policies to limit access to specific types of users.
Control measures
To reduce IT risks, you have many options. IT hazards can be minimized by taking physical security measures, training staff, and providing equipment. To reduce risk, you need to have comprehensive controls that work together. To limit exposure, you must implement administrative controls like job rotation. It is essential to have PPE, such as respirators and goggles. These measures should work in conjunction with each other and be communicated to employees and reviewed on a regular basis.
A risk assessment is essential to determine the best controls for your business. You need to identify and prioritize the most critical risks for your business, then choose the best controls. These measures should not be expensive and must be effective.
Reaction preparation
Workers should be aware of the risks associated with a specific reaction and pay particular attention to safety aspects during reaction preparation. Workers in categories C, D and D should do tasks that don't pose undue risks. However, workers in category A should be cautious about risks related to carcinogens, mutagens, terogens, and pyrophoric substances. Worker should also be aware that explosion risks exist.
FAQ
How does a manager motivate his/her employees?
Motivation can be defined as the desire to achieve success.
Doing something that is enjoyable can help you get motivated.
Another way to get motivated is to see yourself as a contributor to the success of the company.
For example, if you want to become a doctor, you'll probably find it more motivating to see patients than to study medicine books all day.
A different type of motivation comes directly from the inside.
You might feel a strong sense for responsibility and want to help others.
Perhaps you enjoy working hard.
Ask yourself why you aren't feeling motivated.
Next, think of ways you can improve your motivation.
How does Six Sigma work
Six Sigma uses statistical analyses to locate problems, measure them, analyze root cause, fix problems and learn from the experience.
The first step in solving a problem is to identify it.
The data is then analyzed and collected to identify trends.
Next, corrective steps are taken to fix the problem.
Finally, the data are reanalyzed in order to determine if it has been resolved.
This cycle continues until there is a solution.
What are management concepts, you ask?
Management concepts are the principles and practices used by managers to manage people, resources. These topics include job descriptions, performance evaluations and training programs. They also cover human resource policies, job description, job descriptions, job descriptions, employee motivation, compensation systems, organizational structures, and many other topics.
Statistics
- Your choice in Step 5 may very likely be the same or similar to the alternative you placed at the top of your list at the end of Step 4. (umassd.edu)
- The average salary for financial advisors in 2021 is around $60,000 per year, with the top 10% of the profession making more than $111,000 per year. (wgu.edu)
- This field is expected to grow about 7% by 2028, a bit faster than the national average for job growth. (wgu.edu)
- The BLS says that financial services jobs like banking are expected to grow 4% by 2030, about as fast as the national average. (wgu.edu)
- UpCounsel accepts only the top 5 percent of lawyers on its site. (upcounsel.com)
External Links
How To
How do you get your Six Sigma license?
Six Sigma is an effective quality management tool that can improve processes and increase productivity. It's a system that allows companies to get consistent results from operations. The name is derived from the Greek word "sigmas", which means "six". Motorola developed this process in 1986. Motorola realized that it was important to standardize manufacturing processes so they could produce products quicker and cheaper. Because of the number of people involved in the work, they had problems maintaining consistency. To solve this problem, they decided to use statistical tools such as control charts and Pareto analysis. These techniques would be applied to every aspect of the operation. This would allow them to make any necessary changes. The Six Sigma certification process involves three major steps. The first step is to find out if you're qualified. You will need to complete some classes before you can start taking the tests. Once you've passed those classes, you'll start taking the tests. You'll want to study everything you learned during the class beforehand. After that, you can take the test. If you pass, you'll get certified. Finally, you can add your certifications on to your resume.